You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
A question on network router cabling
- Thread starter mikefamig
- Start date
video321 said:6 ports isn't that bad for network drops. Once you add coax is when it really sucks!
You didn't have to go through all that for your XEP. All you needed to do was put a static IP into the computer. A switch doesn't care about subnets.
You know I should have thought of that. i have a few Cisco wireless access points that I have configured with my laptop by putting my wired ethernet connection on my laptop in the 10.0.0.x subnet that they were set to.
DUH!
video321 said:6 ports isn't that bad for network drops.
That is the sort of thing that a DIY'er like me suffers over. I have no idea what is customary or acceptable. You guys are a huge help.
Thanks
wkearney99
Senior Member
video321 said:6 ports isn't that bad for network drops. Once you add coax is when it really sucks!
You got that right. I've got a couple of single gang positions with two coax and two CAT5E and it's brutal trying to get the connectors on there and then into the faceplates. These are on outside walls that are spray foam insulated, so there's no leeway for pushing wires back out of the boxes. Hindsight tells me it'd have been MUCH less trouble to have put the wires into their own 2-gang positions instead of a 2-gang with AC on one half. You live, you learn... and with forums like this YOU SHARE SO OTHERS WON'T SCREW UP like you did...
video321 said:You didn't have to go through all that for your XEP. All you needed to do was put a static IP into the computer. A switch doesn't care about subnets.
There's a little dance with ARP tables, but yes, if you're wired into the same switch you can often get away with having multiple (different) subnets into the same switch fabric. Though it becomes a headache down the line when you can't remember why you tried being so clever... Likewise VLAN setup. One firmware update with a factory reset. months/years later and you're scrambling trying to figure WTF did you set it up that way...
And don't get me started on attempts to be 'clever' when stuff that wants to use multicast for 'easier' setups. As in, all kinds of new IoT-oriented gear....
pete_c
Guru
<p>Here did utilize single and double keystone covers here with single and double LV rings. </p>
<p> </p>
<p>One set up used two Arlington boxes which worked but looked very busy. </p>
<p> </p>
<p> </p>
</p>
<p> </p>
<p>I patched some 6-8 network keystone jacks to one plate to a patch panel. I mostly utilized the extra network connections to tinker with multimedia stuff rather than use a single network to switch thing. Early version also had an RJ11 telephone jack. </p>
<p> </p>
<p>The breakfast nook LCD TV was flush mounted on an outside wall. I did install electric in conduit to the box and had to deal with the insulation which was a PITA. I was impressed though that the in wall box fit nicely in the wall. </p>
<p> </p>
<p>Here had issues using HDMI on the 6 port plates. My resolution for coax (OTA/Inhouse, cable, DTV and DISH) was to use 1 foot thin RG-59 to a coupler inside of the wall before going to the wall plate. I also used them outside of the wall plate to wherever. Worked fine this way. </p>
<p> </p>
<p>HDMI were short runs and they were difficult to deal with such. </p>
<p> </p>
<p>Really just writing that you can do it (I have done it); difficult sometimes as Bill mentions above. </p>
<p> </p>
<p>Relating to Frontier I have nothing good to comment about them and do not really feel like deleting any expletives that I might write regarding their service.</p>
<p> </p>
<p>One set up used two Arlington boxes which worked but looked very busy. </p>
<p> </p>
<p>
 </p>
</p><p> </p>
<p>I patched some 6-8 network keystone jacks to one plate to a patch panel. I mostly utilized the extra network connections to tinker with multimedia stuff rather than use a single network to switch thing. Early version also had an RJ11 telephone jack. </p>
<p> </p>
<p>The breakfast nook LCD TV was flush mounted on an outside wall. I did install electric in conduit to the box and had to deal with the insulation which was a PITA. I was impressed though that the in wall box fit nicely in the wall. </p>
<p> </p>
<p>Here had issues using HDMI on the 6 port plates. My resolution for coax (OTA/Inhouse, cable, DTV and DISH) was to use 1 foot thin RG-59 to a coupler inside of the wall before going to the wall plate. I also used them outside of the wall plate to wherever. Worked fine this way. </p>
<p> </p>
<p>HDMI were short runs and they were difficult to deal with such. </p>
<p> </p>
<p>Really just writing that you can do it (I have done it); difficult sometimes as Bill mentions above. </p>
<p> </p>
<p>Relating to Frontier I have nothing good to comment about them and do not really feel like deleting any expletives that I might write regarding their service.</p>
We had a nightmare experience with Frontier this past week that left me too weak to tell you the extent of it. I even had a tech support guy hang up on me! Another transferred my call to a completely different business. If they don't know how to help you they just disconnect you. I finally got to a service supervisor who got things fixed.
Frontier bought our ISP (ATT U-Verse) and we still have an employee discount with them so we stay with them. We do have Cox Cable and Direct TV as options and we are considering going to Direct TV.
Mike.
Frontier bought our ISP (ATT U-Verse) and we still have an employee discount with them so we stay with them. We do have Cox Cable and Direct TV as options and we are considering going to Direct TV.
Mike.
I had an interesting discovery tonight while configuring cameras. I .set a static IP on the camera and then forwarded a port to the cam in the firewall.
With this done I was able to access the cam via the LAN address 192.168.254.x ort but I could not access it from the WAN using my router address
ort but I could not access it from the WAN using my router address ort. I struggled with anti virus software and some other ideas until i found a post on the net at forums.att.com. It suggested that you need to take your computer/iphone outside the wifi range or otherwise disconnect from the LAN in order to access the cam from the WAN. I turned off wifi on my Iphone and problem solved. Then I disconnected my laptop and it worked too.
ort. I struggled with anti virus software and some other ideas until i found a post on the net at forums.att.com. It suggested that you need to take your computer/iphone outside the wifi range or otherwise disconnect from the LAN in order to access the cam from the WAN. I turned off wifi on my Iphone and problem solved. Then I disconnected my laptop and it worked too.
So can anyone explain this too me? This was not necessary with my old router/gateway.
Mike.
With this done I was able to access the cam via the LAN address 192.168.254.x
So can anyone explain this too me? This was not necessary with my old router/gateway.
Mike.
pete_c
Guru
You need a basic understanding relating the what a firewall / router does.
It is not complicated and simple in process and implementation and use.
Let's draw a picture of your network so that you can understand it's functionality. Baby steps. It is very logical and all makes sense.
From the wiki Firewall.
In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules.[1] A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed not to be secure or trusted.[2] Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls filter traffic between two or more networks; they are either software appliances running on general purpose hardware, or hardware-based firewall computer appliances. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine.[3][4] Firewall appliances may also offer other functionality to the internal network they protect, such as acting as a DHCP[5][6] or VPN[7][8][9][10] server for that network.
The Frontier box (router) you have is a combination modem/router, firewall, network switch and wireless access point. That and a typical box is actually two routers. One part on the ISP side you do not see and cannot change. The other part you can see and change.
Combining these features in one box is common and has been utilized now for many years.
One part of the box provides you with one internet addess given to you by your ISP provider. The other part uses that internet address and NAT to provide you with multiple addresses / devices in your home.
Between the interfaces you can configure what goes in and out of the internet.
The features / functionality are basically the same on any firewall. Some are more granular and some are simple with an assumption of typical rules.
Here is a basic drawing. Looking for a better picture.
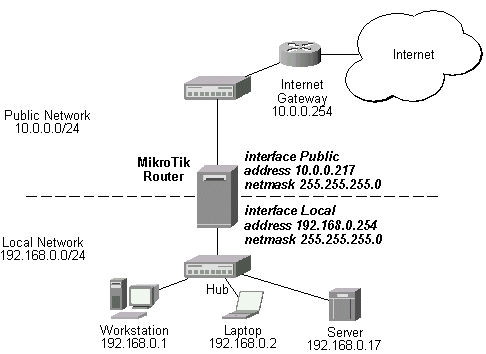
It is not complicated and simple in process and implementation and use.
Let's draw a picture of your network so that you can understand it's functionality. Baby steps. It is very logical and all makes sense.
From the wiki Firewall.
In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules.[1] A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed not to be secure or trusted.[2] Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls filter traffic between two or more networks; they are either software appliances running on general purpose hardware, or hardware-based firewall computer appliances. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine.[3][4] Firewall appliances may also offer other functionality to the internal network they protect, such as acting as a DHCP[5][6] or VPN[7][8][9][10] server for that network.
The Frontier box (router) you have is a combination modem/router, firewall, network switch and wireless access point. That and a typical box is actually two routers. One part on the ISP side you do not see and cannot change. The other part you can see and change.
Combining these features in one box is common and has been utilized now for many years.
One part of the box provides you with one internet addess given to you by your ISP provider. The other part uses that internet address and NAT to provide you with multiple addresses / devices in your home.
Between the interfaces you can configure what goes in and out of the internet.
The features / functionality are basically the same on any firewall. Some are more granular and some are simple with an assumption of typical rules.
Here is a basic drawing. Looking for a better picture.

I did a little reading on NAT reflection and am confused.video321 said:Simple... some routers will perform what is called NAT Reflection and some won't.
It seems to me that WITH NAT reflection the source device (my pc) and the destination device (my cam) will be assigned adresses on the same private network and be able to communicate with each other without ever leaving the private network and without ever crossing the firewall to the WAN.
It also seems to me that WITHOUT NAT reflection the packets between my pc and my cam would travel out across the router firewall to the WAN net and then come back through the router firewall and to the camera.
Reflection keeps the packets inside the private network and without it the trip is longer but should still work, no?
Mike.
Not quite...
NAT reflection doesn't affect the IP addresses assigned - that's entirely up to you actually. The devices can be on different networks for that matter, but they will have internal IPs.
NAT reflection enables your router/firewall to intercept the traffic created by an internal node that is destined for another internal node by reading the destination IP (your WAN IP) and matching a port forward with it. Then it will simply redirect the connection to the destination. So what happens is your internal laptop says... connect to 156.23.23.11 on port 80. As this traffic goes across the router it reads it and says hey! I know that IP -- it's my WAN! -- and also sees port 80 is open and forwarded to another internal node. The router will then simply "redirect" the connection to that particular node. Not to confuse you any further, but remember... the node that port 80 is being redirected to can be any network the router is aware of. So your laptop can be on 192.168.1.x and the node you want to connect on can be on 192.168.100.x.
I hope that makes sense.
NAT reflection doesn't affect the IP addresses assigned - that's entirely up to you actually. The devices can be on different networks for that matter, but they will have internal IPs.
NAT reflection enables your router/firewall to intercept the traffic created by an internal node that is destined for another internal node by reading the destination IP (your WAN IP) and matching a port forward with it. Then it will simply redirect the connection to the destination. So what happens is your internal laptop says... connect to 156.23.23.11 on port 80. As this traffic goes across the router it reads it and says hey! I know that IP -- it's my WAN! -- and also sees port 80 is open and forwarded to another internal node. The router will then simply "redirect" the connection to that particular node. Not to confuse you any further, but remember... the node that port 80 is being redirected to can be any network the router is aware of. So your laptop can be on 192.168.1.x and the node you want to connect on can be on 192.168.100.x.
I hope that makes sense.
drvnbysound
Senior Member
My eyes were opened to the NAT reflection stuff when I went from a consumer grade Linksys 54G router/AP to an enterprise Cisco Integrated Services Router. I was kinda shocked that the "enterprise" solution didn't offer such "simple" functionality; with the Linksys it was default configuration that I never enabled.
Mike, FWIW, in my part of the country, DirectTV's internet offering is ATT U-Verse; not sure if that's the same everywhere, but something worth checking into. If so, you have one less option...
Mike, FWIW, in my part of the country, DirectTV's internet offering is ATT U-Verse; not sure if that's the same everywhere, but something worth checking into. If so, you have one less option...
pete_c
Guru
Back to the Wiki here...
NAT loopback, also known as NAT hairpinning or NAT reflection,[9] is a feature in many consumer routerswhich permits the access of a service via the public IP address from inside the local network. This eliminates the need for using separate domain name resolution for hosts inside the network than for the public network for a website, for example.
The following describes an example network:
If no applicable DNAT rule is available, the router drops the packet. An ICMP Destination Unreachable reply may be sent. If any DNAT rules were present, address translation is still in effect; the router still rewrites the source IP address in the packet. The local computer (192.168.1.100) sends the packet as coming from 192.168.1.100, but the server (192.168.1.2) receives it as coming from 203.0.113.1. When the server replies, the process is identical as for an external sender. Thus, two-way communication is possible between hosts inside the LAN network via the public IP address.
Consumer routers can have this shut off or not offer an option for your own safety (it is said). Here using PFSense there is a switch for it. Firmware DD-WRT / OpenWRT also has a switch for it.
The primary reason for the security concern is that some consumer routers appear to intentionally disable NAT loopback by default, and there is no way around this with stock firmware. However, this is not an intentional barrier, it’s just a constraint of limited stock firmware. Nothing new there.
Don’t be fooled by the plethora of forum posts crying that NAT loopback is disabled on routers purposefully, that it opens up dangerous security holes, or that it will destroy your network and ultimately your livelihood as you know it. Like the vast majority of scare tactic-based content on the internet, it’s false. Your router will not stab you in your sleep if you allow NAT loopback … although it may emit higher levels of radiation.....
Looks like your new box doesn't have NAT reflection or a switch for it.
NAT loopback, also known as NAT hairpinning or NAT reflection,[9] is a feature in many consumer routerswhich permits the access of a service via the public IP address from inside the local network. This eliminates the need for using separate domain name resolution for hosts inside the network than for the public network for a website, for example.
The following describes an example network:
- Public address: 203.0.113.1. This is the address of the WAN interface on the router.
- Internal address of router: 192.168.1.1
- Address of the server: 192.168.1.2
- Address of a local computer: 192.168.1.100
If no applicable DNAT rule is available, the router drops the packet. An ICMP Destination Unreachable reply may be sent. If any DNAT rules were present, address translation is still in effect; the router still rewrites the source IP address in the packet. The local computer (192.168.1.100) sends the packet as coming from 192.168.1.100, but the server (192.168.1.2) receives it as coming from 203.0.113.1. When the server replies, the process is identical as for an external sender. Thus, two-way communication is possible between hosts inside the LAN network via the public IP address.
Consumer routers can have this shut off or not offer an option for your own safety (it is said). Here using PFSense there is a switch for it. Firmware DD-WRT / OpenWRT also has a switch for it.
The primary reason for the security concern is that some consumer routers appear to intentionally disable NAT loopback by default, and there is no way around this with stock firmware. However, this is not an intentional barrier, it’s just a constraint of limited stock firmware. Nothing new there.
Don’t be fooled by the plethora of forum posts crying that NAT loopback is disabled on routers purposefully, that it opens up dangerous security holes, or that it will destroy your network and ultimately your livelihood as you know it. Like the vast majority of scare tactic-based content on the internet, it’s false. Your router will not stab you in your sleep if you allow NAT loopback … although it may emit higher levels of radiation.....
Looks like your new box doesn't have NAT reflection or a switch for it.
video321 said:Not quite...
NAT reflection doesn't affect the IP addresses assigned - that's entirely up to you actually. The devices can be on different networks for that matter, but they will have internal IPs.
NAT reflection enables your router/firewall to intercept the traffic created by an internal node that is destined for another internal node by reading the destination IP (your WAN IP) and matching a port forward with it. Then it will simply redirect the connection to the destination. So what happens is your internal laptop says... connect to 156.23.23.11 on port 80. As this traffic goes across the router it reads it and says hey! I know that IP -- it's my WAN! -- and also sees port 80 is open and forwarded to another internal node. The router will then simply "redirect" the connection to that particular node. Not to confuse you any further, but remember... the node that port 80 is being redirected to can be any network the router is aware of. So your laptop can be on 192.168.1.x and the node you want to connect on can be on 192.168.100.x.
I hope that makes sense.
And what happens to the same packet in the example above if you don't have NAT reflection on the router?
Similar threads
- Replies
- 12
- Views
- 452
- Replies
- 5
- Views
- 511
