Got a couple new cameras and having trouble blocking them from WAN access. I put them on the network to get their MAC to do the DHCP assignments. Already has an alias for other cams that had a blocking rule so added the IP's to the list. Found the IP already had some states so deleted them but it just creates more. Guess I need to read up on this or maybe someone here can help...
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
blocking cameras in pfsense
- Thread starter JimS
- Start date
-
- Tags
- cctv ip cameras nvr
I suppose I could do that although it is very easy to just plug them in anywhere. I did order 4 strand fiber for the detached garage so I could run the cameras on the spare 2 strands. What's the reason for separation - security, reducing traffic on the main network, or both?Any IP cameras should be plugged into an isolated environment. If you plan on using a PC based NVR (you really should), then add a 2nd NIC to this PC, so it can access the cameras, and the rest of your infrastructure without complex rues.
Ordered the end terminators for the extra pair of fiber strands and network card to do a separate network for the cameras.
I should read up on vlans. Not using them now and know nothing about them. My block rule was to wan network. Didn't realize that doesn't block everything on the wan port. Changed destination to any and now it works. Still seems confusing to me as it's a lan rule and blocks to any which would include other lan devices? So wouldn't that block the camera from getting time from the pfsense time server?
I should read up on vlans. Not using them now and know nothing about them. My block rule was to wan network. Didn't realize that doesn't block everything on the wan port. Changed destination to any and now it works. Still seems confusing to me as it's a lan rule and blocks to any which would include other lan devices? So wouldn't that block the camera from getting time from the pfsense time server?
Frunple
Active Member
Vlans are nothing but another network that shares a common switch. Don't over think them.
Take a switch, if you have a 24 port switch and are only using ten ports on it, but you need to add another network, instead of going out and buying another switch you can use a vlan to utilize the other ports on the switch. Vlans make one switch act as 2, or more, switches.
The way you would do this is by using a trunk port. Trunks carry multiple vlans. So on the pfSense you would add a vlan (say vlan10) with your LAN interface as parent. This makes the LAN interface a trunk with your LAN being untagged, and vlan10 being tagged. Untagged means any traffic that isn't tagged with a vlan id will use the untagged vlan, also know as pvid (port vlan ID).
So on your switch, whichever port is connected to the pfSense LAN needs to be a trunk also. In this example it would have the pvid untagged and 10 tagged.
That gets both LANS to your switch, to access vlan10 you would need to untag vlan 10 on any ports you need it on. You now have 2 switches by using one. Make sense?
Keep in mind, a tagged port needs to be plugged into a tagged port. So if you tag vlan10 on port 13 and plug a pc into it, it won't use vlan13 unless you tag 10 on the PC's interface. That's why you would untag 10 on access ports used by vlan 10.
That would not block other devices since they are all on the same layer 2 segment. Layer 2 is switching, layer 3 is routing. When you access your cameras from your LAN, the traffic doesn't even go to your router. It hits a switchport and is sent to another switchport only.
Yes, that rule would block NTP. You would have to add a pass rule above that one with your cameras (add an alias with all camera IP's in it) as source, and LAN net as destination on port 123. But your best bet is to allow your NVR to port 123, then sync all cameras to the NVR.
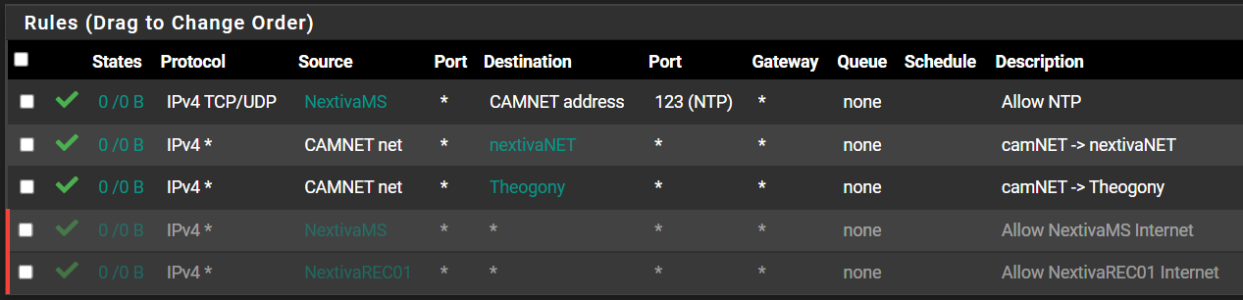
Here's my Camera Rules attached.
The top one is my NVR time sync.
Next allows my CAMNet access to an offsite recorder over a vpn.
Next allows cameras to iSCSI storage device.
That's all. Nothing else needed.
The bottom 2 are to allow the NVR and recorder access to the internet to do updates. I leave them disabled until needed.
Take a switch, if you have a 24 port switch and are only using ten ports on it, but you need to add another network, instead of going out and buying another switch you can use a vlan to utilize the other ports on the switch. Vlans make one switch act as 2, or more, switches.
The way you would do this is by using a trunk port. Trunks carry multiple vlans. So on the pfSense you would add a vlan (say vlan10) with your LAN interface as parent. This makes the LAN interface a trunk with your LAN being untagged, and vlan10 being tagged. Untagged means any traffic that isn't tagged with a vlan id will use the untagged vlan, also know as pvid (port vlan ID).
So on your switch, whichever port is connected to the pfSense LAN needs to be a trunk also. In this example it would have the pvid untagged and 10 tagged.
That gets both LANS to your switch, to access vlan10 you would need to untag vlan 10 on any ports you need it on. You now have 2 switches by using one. Make sense?
Keep in mind, a tagged port needs to be plugged into a tagged port. So if you tag vlan10 on port 13 and plug a pc into it, it won't use vlan13 unless you tag 10 on the PC's interface. That's why you would untag 10 on access ports used by vlan 10.
That would not block other devices since they are all on the same layer 2 segment. Layer 2 is switching, layer 3 is routing. When you access your cameras from your LAN, the traffic doesn't even go to your router. It hits a switchport and is sent to another switchport only.
Yes, that rule would block NTP. You would have to add a pass rule above that one with your cameras (add an alias with all camera IP's in it) as source, and LAN net as destination on port 123. But your best bet is to allow your NVR to port 123, then sync all cameras to the NVR.
Here's my Camera Rules attached.
The top one is my NVR time sync.
Next allows my CAMNet access to an offsite recorder over a vpn.
Next allows cameras to iSCSI storage device.
That's all. Nothing else needed.
The bottom 2 are to allow the NVR and recorder access to the internet to do updates. I leave them disabled until needed.
Attachments
Last edited:
I got it working but may need more help later. Thanks!If you can confirm which direction you're trying to block, and share us a screenshot of your rules (sanitized), we can take a look. A proper rule should block everything. A copy of the states may be helpful as well.
Thanks for explaining that. Very helpful!Vlans are nothing but another network that shares a common switch. Don't over think them.
Take a switch, if you have a 24 port switch and are only using ten ports on it, but you need to add another network, instead of going out and buying another switch you can use a vlan to utilize the other ports on the switch. Vlans make one switch act as 2, or more, switches.
The way you would do this is by using a trunk port. Trunks carry multiple vlans. So on the pfSense you would add a vlan (say vlan10) with your LAN interface as parent. This makes the LAN interface a trunk with your LAN being untagged, and vlan10 being tagged. Untagged means any traffic that isn't tagged with a vlan id will use the untagged vlan, also know as pvid (port vlan ID).
So on your switch, whichever port is connected to the pfSense LAN needs to be a trunk also. In this example it would have the pvid untagged and 10 tagged.
That gets both LANS to your switch, to access vlan10 you would need to untag vlan 10 on any ports you need it on. You now have 2 switches by using one. Make sense?
Keep in mind, a tagged port needs to be plugged into a tagged port. So if you tag vlan10 on port 13 and plug a pc into it, it won't use vlan13 unless you tag 10 on the PC's interface. That's why you would untag 10 on access ports used by vlan 10.
That would not block other devices since they are all on the same layer 2 segment. Layer 2 is switching, layer 3 is routing. When you access your cameras from your LAN, the traffic doesn't even go to your router. It hits a switchport and is sent to another switchport only.
Yes, that rule would block NTP. You would have to add a pass rule above that one with your cameras (add an alias with all camera IP's in it) as source, and LAN net as destination on port 123. But your best bet is to allow your NVR to port 123, then sync all cameras to the NVR.
Here's my Camera Rules attached.
The top one is my NVR time sync.
Next allows my CAMNet access to an offsite recorder over a vpn.
Next allows cameras to iSCSI storage device.
That's all. Nothing else needed.
The bottom 2 are to allow the NVR and recorder access to the internet to do updates. I leave them disabled until needed.
Similar threads
- Replies
- 6
- Views
- 1K