Back to the Wiki here...
NAT loopback, also known as
NAT hairpinning or
NAT reflection,
[9] is a feature in many consumer routerswhich permits the access of a service via the public IP address from inside the local network. This eliminates the need for using separate domain name resolution for hosts inside the network than for the public network for a website, for example.
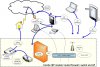
The following describes an example network:
- Public address: 203.0.113.1. This is the address of the WAN interface on the router.
- Internal address of router: 192.168.1.1
- Address of the server: 192.168.1.2
- Address of a local computer: 192.168.1.100
If a packet is sent to the public address by a computer at 192.168.1.100, the packet would normally be routed to the
default gateway (the router), unless an explicit route is set in the computer's
routing tables. A router with the NAT loopback feature detects that 203.0.113.1 is the address of its WAN interface, and treats the packet as if coming from that interface. It determines the destination for that packet, based on DNAT (port forwarding) rules for the destination. If the data were sent to port 80 and a DNAT rule exists for port 80 directed to 192.168.1.2, then the host at that address receives the packet.
If no applicable DNAT rule is available, the router drops the packet. An
ICMP Destination Unreachable reply may be sent. If any DNAT rules were present, address translation is still in effect; the router still rewrites the source IP address in the packet. The local computer (192.168.1.100) sends the packet as coming from 192.168.1.100, but the server (192.168.1.2) receives it as coming from 203.0.113.1. When the server replies, the process is identical as for an external sender. Thus, two-way communication is possible between hosts inside the LAN network via the public IP address.
Consumer routers can have this shut off or not offer an option for your own safety (it is said). Here using PFSense there is a switch for it. Firmware DD-WRT / OpenWRT also has a switch for it.
The primary reason for the security concern is that some consumer routers appear to intentionally disable NAT loopback by default, and there is no way around this with stock firmware. However, this is not an intentional barrier, it’s just a constraint of limited stock firmware. Nothing new there.
Don’t be fooled by the plethora of forum posts crying that NAT loopback is disabled on routers purposefully, that it opens up dangerous security holes, or that it will destroy your network and ultimately your livelihood as you know it. Like the vast majority of scare tactic-based content on the internet, it’s false. Your router will not stab you in your sleep if you allow NAT loopback … although it may emit higher levels of radiation.....
Looks like your new box doesn't have NAT reflection or a switch for it.